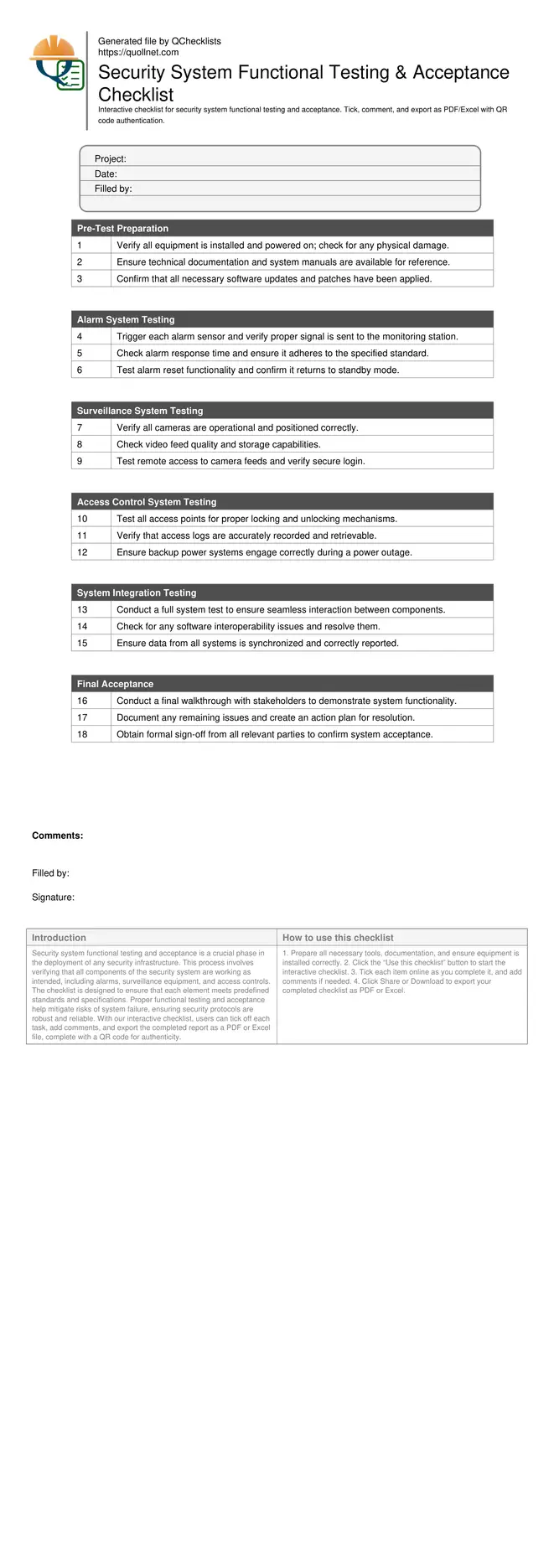
Security System Functional Testing and Acceptance
Security system functional testing and acceptance is a crucial phase in the deployment of any security infrastructure. This process involves verifying that all components of the security system are working as intended, including alarms, surveillance equipment, and access controls. The checklist is designed to ensure that each element meets predefined standards and specifications. Proper functional testing and acceptance help mitigate risks of system failure, ensuring security protocols are robust and reliable. With our interactive checklist, users can tick off each task, add comments, and export the completed report as a PDF or Excel file, complete with a QR code for authenticity.
- Ensure all security components function correctly and meet specifications.
- Identify and mitigate risks associated with system failures.
- Interactive online checklist with tick, comment, and export features secured by QR code.
- Facilitate comprehensive documentation and stakeholder communication.
Pre-Test Preparation
Alarm System Testing
Surveillance System Testing
Access Control System Testing
System Integration Testing
Final Acceptance
Importance of Functional Testing
Functional testing of security systems is essential to ensure that each component operates as expected under real-world conditions. This step is critical in identifying any issues that could compromise the system's integrity or reliability. By conducting thorough testing, organizations can prevent costly security breaches and ensure compliance with industry standards.
- Verify operational status of all security components.
- Ensure compliance with industry standards and regulations.
- Identify potential vulnerabilities before system deployment.
Steps for Effective Testing
Effective security system testing requires a structured approach. Begin with pre-test preparations, ensuring all equipment is ready and documentation is available. Conduct individual component tests followed by system integration checks. Finally, perform a comprehensive acceptance test with stakeholders.
- Prepare equipment and documentation before testing.
- Test individual components and system integration.
- Engage stakeholders in the final acceptance process.
How to Use the Security System Testing Checklist
- Prepare all necessary tools, documentation, and ensure equipment is installed correctly.
- Click the “Use this checklist” button to start the interactive checklist.
- Tick each item online as you complete it, and add comments if needed.
- Click Share or Download to export your completed checklist as PDF or Excel.
Call to Action
- Start Checklist Tick off tasks, leave comments on items or the whole form, and export your completed report to PDF or Excel—with a built-in QR code for authenticity.
- Download Excel - Security System Functional Testing and Acceptance
- Download PDF - Security System Functional Testing and Acceptance
- View Image - Security System Functional Testing and Acceptance